Fantastic What Is A Non Technical Method That A Cybercriminal

The best way to protect yourself is to simply hang up.
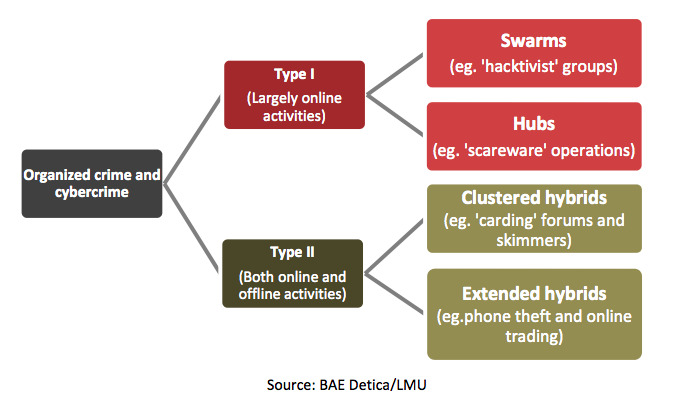
What is a non technical method that a cybercriminal. Attack vector A specific method used by a cybercriminal to infiltrate a system. Giving the appearance of being escorted by an authorized individual Joining a crowd pretending to be a member. There is an extensive array of common attack methods available to the cybercriminal.
Managerial strategic and high-level general audience. These range from off the shelf virus and Trojan software products simple email and website deception techniques through to online-purchases of already exploited computers and personal and financial data. Is a completely non-technical means for a criminal to gather information on a target is an attack that attempts to manipulate individuals into performing actions or divulging confidential information.
Managerial strategic and high-level general audience. What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization. The aim of this paper is to extend the authors earlier research that first introduced the concept of the Cybercrime Execution Stack by examining in detail the underlying data objectives of the cybercriminal.
The cybercriminal looks for weaknesses in the companys security people systems or network. It is designed to test the skills and knowledge presented in the course. Non-technical means for a criminal to gather information on a target.
What is an example of early warning systems that can be used to thwart cybercriminals. Cybersecurity Essentials 11 Final Quiz Answers Form B 100 2018 What is an example of early warning systems that can be used to thwart cybercriminals. The following is a listing of just some of the most common methods identity criminals have been known to use to obtain your personal identifiable information.
What is a nontechnical method that a cybercriminal would use to gather sensitive information from an organization. Both technical and non-technical law enforcement investigators need the ability to contextualise and structure the illicit activities of the cybercriminal in order to communicate this. The cybercriminal makes initial contact using either a network or social attack.